Best practices for sharing complex Airtable bases securely
When an Airtable base grows in complexity, sharing it becomes risky.
You may have linked records across many tables, automations that should never be touched, and sensitive fields that only a few people should be able to see. Simply inviting everyone into the base as editors is rarely the right approach.
When users are invited directly into a base, even with restricted permissions, a key problem tends to appear.
Field level control is limited. Even if someone is only meant to edit a few fields in a table, they can still see every field in that table, including fields they should not have access to.
Use Interfaces instead of base access
The best practice for sharing Airtable data is to avoid sharing the base at all. Instead, use Airtable Interfaces and invite users to the Interface.
Interfaces act as a controlled layer on top of your base. They allow you to decide exactly what users can see and what they can edit, without exposing the full data model.
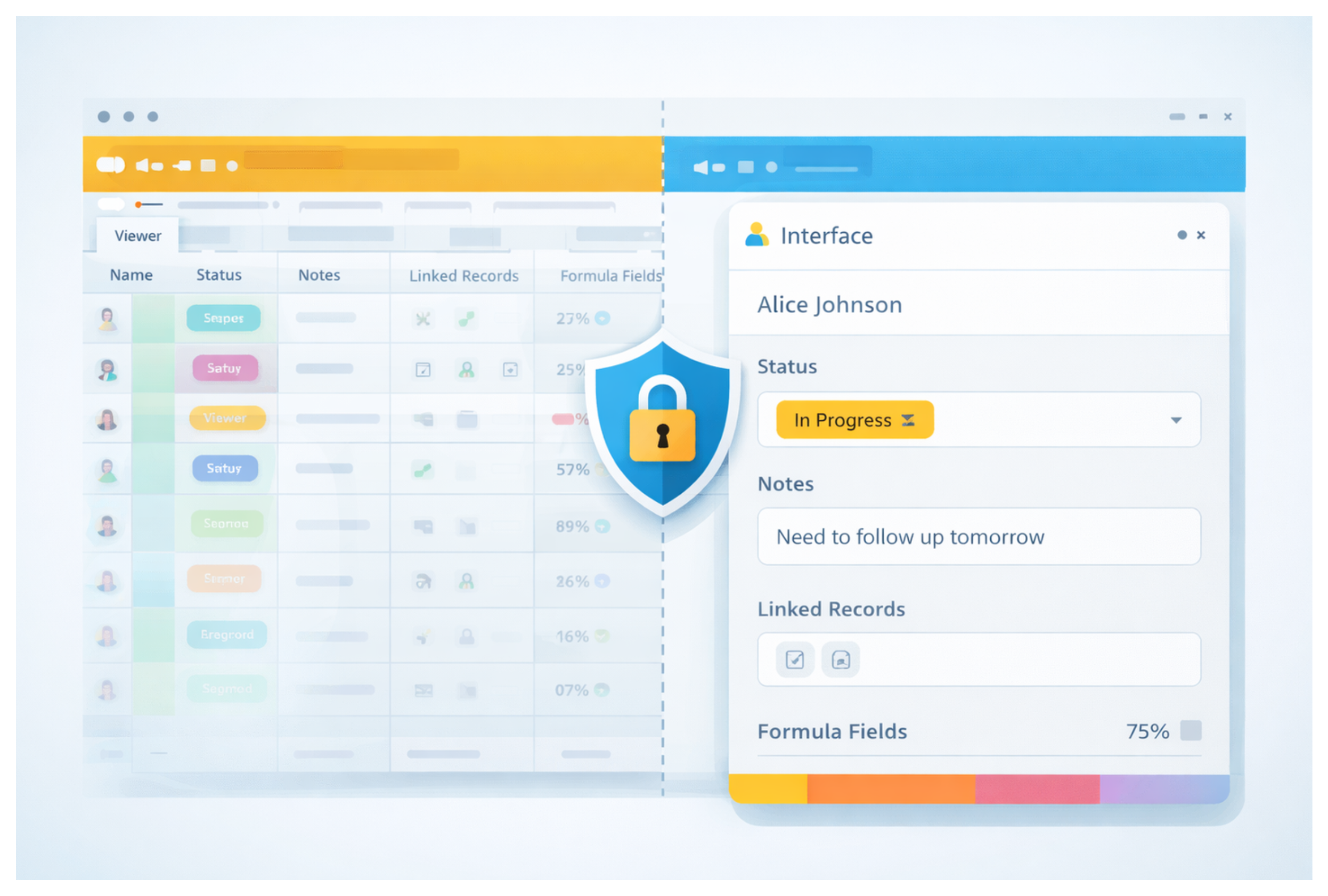
Interfaces let you display only the fields that matter for a specific role.
For example, a stakeholder might only need to update a status field and add notes. In an Interface, you can show just those fields and hide everything else, including formulas, rollups, and system fields.
This greatly reduces the risk of accidental edits.
Record level access using filters
Interfaces also support record level filtering based on the logged in user.
For example, you can filter records so a user only sees records linked to their own user record or email address. This is especially useful for client portals or team specific workflows.
Each user sees only the data that is relevant to them, while the underlying base remains centralized and consistent.
What Interfaces do not allow
Users who are invited only to Interfaces cannot create or manage automations. They also cannot modify tables, fields, or views in the base.
In most cases, this is a good thing. Automations and schema changes should be owned by a small group of administrators who understand the system.
If someone needs to build automations or restructure tables, they should be granted base access intentionally and temporarily, not by default.
A simple sharing strategy that scales
A reliable pattern for sharing complex bases looks like this.
-
Keep the base private for builders and administrators only.
-
Create Interfaces for each role or stakeholder group.
-
Expose only the fields and records each role needs.
-
Make critical fields read only whenever possible.
This approach keeps your data model clean, your automations stable, and your users productive without putting the system at risk.